TACTFlow - Part 0x2. Initial Access
Initial Access - The Hacker’s Front Door
Introduction
Buckle up and grab your fuel of choice; coffee, tea, juice, or just sheer determination, because this is going to be a long one. By the time we’re done, you’ll understand how attackers break in, how defenders try to stop them, and why security teams are basically running on caffeine and adrenaline.
Today, we’re kicking things off with Initial Access: the digital equivalent of sneaking, scamming, or smashing your way into a target. Sometimes attackers slide in unnoticed, sometimes they talk their way through the front door, and sometimes they just send an email with a polite request to click something malicious. Either way, once they’re in, the real fun (or chaos, depending on which side you’re on) begins.
Let’s break, defend, and hack our way through it.
Initial Access - The Hacker’s Front Door
What is Initial Access ?
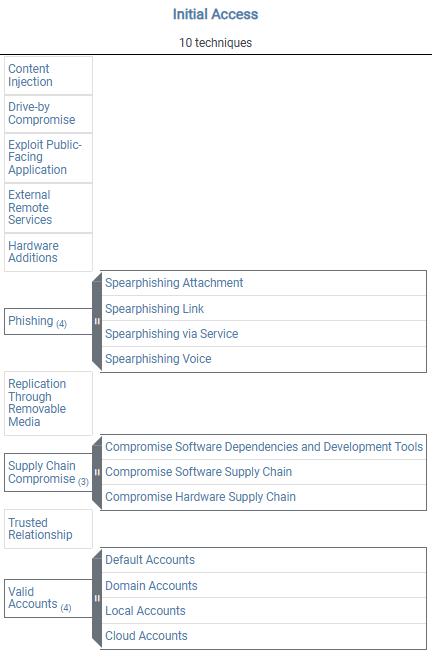
Initial Access is the first step of a cyber attack where an adversary gains entry into a target environment. In the MITRE ATT&CK framework (version 14), Initial Access consists of 10 techniques, ranging from phishing and exploiting vulnerable applications to more advanced methods like supply chain compromise.
If cyber attacks were heist movies, Initial Access would be the part where the con artist smooth-talks their way past the guards, the hacker disables the security cameras, or the crew sneaks in through an unguarded vent. No matter how they do it, the goal is the same: Get in.
For defenders, stopping an attacker here means stopping the breach before it even begins.
How Initial Access Fits Into the TACTFlow Framework
Every attack starts with Initial Access, but how does each team in TACTFlow deal with it?
Cyber Threat Intelligence (CTI) – The Sentinels
CTI teams track, analyze, and predict how attackers gain access. They answer questions like:
- What Initial Access techniques are threat actors using right now?
- Which industries are being targeted?
- Are attackers exploiting vulnerabilities or relying on social engineering?
The goal? Keep Red Teamers updated on real attack methods and ensure the SOC is ready to detect them.
Red Teaming – The Challengers
Red Teamers simulate exactly what real attackers would do. Their mission? Find a way, in preferably one, that security teams aren’t prepared for.
- Phishing emails? Sent.
- Malicious links? Delivered.
- Exploit attempt? Launched.
But a good Red Team doesn’t just break in; they help organizations harden their defenses by testing them in realistic scenarios.
SOC & SOC Engineering – The Defenders
The SOC (Security Operations Center) has one job: Stop the breach before it happens.
- Phishing email detected? Blocked.
- Suspicious login attempt? Flagged.
- Exploit attempt on a web server? Denied.
And when something does slip through? SOC Engineers step in to fine-tune defenses, making sure that trick never works again.
MITRE ATT&CK v14 - The 10 Ways Attackers Get In
We are working with MITRE ATT&CK v14, which defines 10 different techniques under the Initial Access tactic. Here’s what we’re dealing with:
Phishing: Current Under Fire: Breaking Down the Technique !
Phishing (T1566) – “Click Here for a Free Disaster”
The classic social engineering attack, convincing a user to click, download, or hand over credentials. This includes:- Phishing - Spearphishing Attachment (T1566.001)
- Spearphishing Link
- Spearphishing via Service
- Spearphishing Voice (Vishing)
Drive-by Compromise – “Just Visiting the Wrong Website Can Get You Hacked”
No need to click or download anything, just visiting a compromised site can be enough. Attackers inject malicious scripts into legitimate pages, waiting for victims to land there.Exploit Public-Facing Application – “You Forgot to Patch, Didn’t You?”
Attackers scan the internet for vulnerable web apps, VPNs, or exposed services. If your software isn’t up to date, they’ll walk right in.External Remote Services – “Remote Access Without the Security Checks”
Exploiting misconfigured or compromised remote access services like RDP, SSH, or VPN to gain entry. If attackers have valid credentials, they can slip in unnoticed.Hardware Additions – “Hacked Before You Even Turned It On”
Sometimes, the attack starts with a malicious device: USB sticks, rogue network devices, or even backdoored hardware components shipped directly to the target.Content Injection – “The Web Is a Dangerous Place”
Attackers modify legitimate websites to inject malicious content: changing login forms, embedding rogue JavaScript, or redirecting users to phishing pages.Replication Through Removable Media – “USBs Are Not Your Friends”
Malware spreads via infected USB drives, external hard drives, or even SD cards. This technique has been used in some of the world’s most famous cyberattacks.Supply Chain Compromise – “Hacking the Vendors to Hack You”
Instead of attacking a company directly, threat actors compromise a trusted third-party like a software vendor, cloud provider, or hardware supplier to gain access.Trusted Relationship – “When Your Partners Become Your Weakness” Organizations rely on external partners, suppliers, and contractors. Attackers compromise these trusted entities to get into a target’s network through shared access.
Valid Accounts – “Logging In Instead of Breaking In”
If attackers can steal or guess real credentials, they don’t need to hack anything, they just log in like a regular user.
How We’re Implementing These in TACTFlow
For each Initial Access technique, we’ll break it down in TACTFlow by covering:
- How it’s used by attackers (real-world examples).
- How Red Teamers simulate it.
- How SOC teams detect and defend against it.
This project isn’t just about understanding the attacks. It’s about building better defenses, improving SOC detection capabilities, and ensuring Red Teams are simulating the latest threats realistically.