TACTFlow - Part 0x1. Everything is connected ...
TACTFlow - Bridging Intelligence and Action
TACTFlow ?
So, you’re probably thinking: What in the world is “TACTFlow” ? 🤔
Before we dive deep into the nitty-gritty, let’s break it down in a way even your non-tech-savvy cousin could get!
TACTFlow is like the secret handshake between different Cybersec teams, like Cyber Threat Intelligence (CTI), Red Teaming, and SOC Engineering—bringing them all together using Tactics, Techniques, and Procedures (TTPs). Think of it as the glue that makes sure everyone’s on the same page—whether you’re launching cyber attacks, defending against them, or just figuring out who’s trying to mess with your systems.
The name TACTFlow comes from the combination of Tactics—the strategies behind how we approach cyber threats—and Flow, which represents the smooth, continuous exchange of information and actions between the key players (CTI, Red Teaming, and SOC, .. etc). It’s all about making sure the right intel flows seamlessly across teams so everyone can stay one step ahead.
Curious now? Let’s go ahead and unwrap the magic behind TACTFlow.
Bridging CTI, Red Teaming, and SOC: Tackling Common Challenges
In recent years, the collaboration between diffrent cyebrsecurity teams, like Cyber Threat Intelligence (CTI), Red Teaming, SOC & SOC Engineering become a critical task for building a strong defense against adversaries. However, based on my research and experience working in this field, I’ve noticed that many professionals face significant challenges when trying to connect these disciplines effectively.
For instance, junior Red Teamers often struggle to translate TTPs (Tactics, Techniques, and Procedures) provided by CTI analysts into actionable attack simulations. Similarly, SOC teams frequently find it difficult to interpret logs and events generated during Red Team exercises, limiting their ability to improve detection and response mechanisms.
In this series of articles, it is my job to tackle these issues by presenting the relationships between CTI, Red Teaming, and SOC Engineering. We’ll break down each discipline, define their key processes, and highlight how they interact through the shared language of TTPs. By doing so, I hope to make these concepts more accessible and provide practical solutions for overcoming common pain points.
Whether you’re a CTI analyst, Red Teamer, or SOC engineer, this series of articles, will offer valuable insights into how to bridge the gaps between these roles and strengthen your cybersecurity strategy.
If you’re ready to roll, let’s dive in, one step at a time .. no running, just walking through the fun!
CTI, Red Teaming, and SOC Engineering: How Do They Connect?
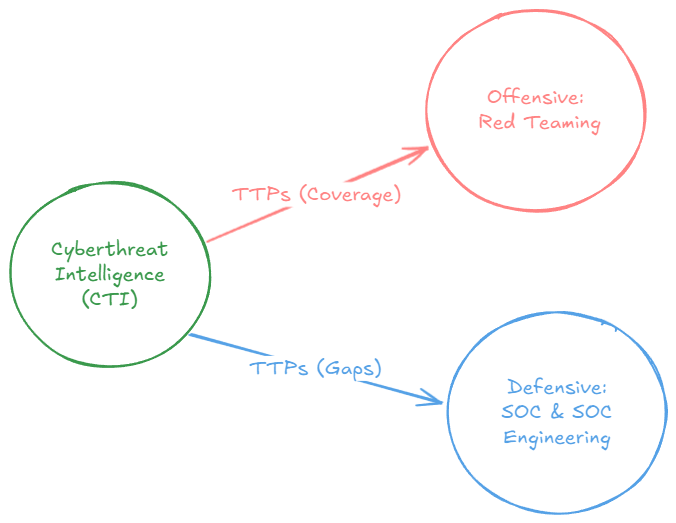
The critical link between Cyber Threat Intelligence (CTI), Red Teaming, and SOC Engineering lies in Tactics, Techniques, and Procedures (TTPs). CTI analysts, after analyzing threats or conducting threat landscape assessments, identify organizational defenses’ strengths and weaknesses. These insights—whether identifying coverage or gaps, help bridge the divide between offense (Red Teaming) and defense (SOC Engineering). The connection is further solidified through the generation of actionable TTPs, which serve as a universal language between these domains.
To fully understand this relationship, we must first break down each of these fields and their processes.
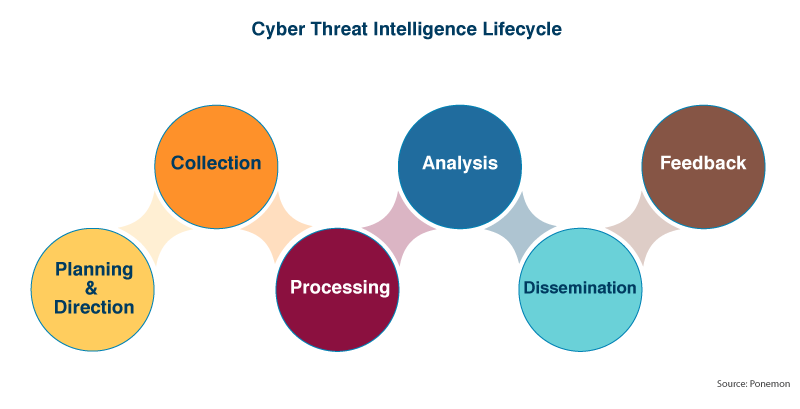
1. The CTI Cycle
The Cyber Threat Intelligence (CTI) cycle is a structured approach to gathering, analyzing, and disseminating intelligence about potential cyber threats. It consists of the following stages:
Requirements Definition:
Identify the specific intelligence needs of the organization. This could include understanding threats targeting specific assets, industries, or geographical regions.Data Collection:
Gather data from various sources, such as open-source intelligence (OSINT), dark web monitoring, telemetry from organizational assets, threat feeds, and historical incidents.Analysis and Processing:
Transform raw data into actionable intelligence. Analysts use frameworks like MITRE ATT&CK to map threat behaviors and identify the tactics, techniques, and procedures (TTPs) of adversaries.Dissemination:
Share the intelligence with relevant teams, such as Red Teams for simulation purposes or SOC teams for defensive adjustments. The goal is to ensure the intelligence informs actionable outcomes, such as simulated attacks or defensive detections.Feedback Loop:
Use feedback from end-users (e.g., Red Teamers, SOC engineers) to refine future intelligence cycles and improve the relevance of findings.
2. The Red Teaming Cycle
The Red Teaming cycle involves simulating adversarial tactics to evaluate an organization’s defenses. The key stages are:
Reconnaissance:
Conduct thorough reconnaissance to identify potential targets and vulnerabilities. This includes scanning for misconfigurations, open ports, unpatched systems, and human vulnerabilities (e.g., phishing targets).Planning:
Develop a detailed attack plan based on the gathered intelligence. Red Teamers may use TTPs derived from CTI to emulate specific threat actors.Execution:
Execute the planned attack, using tools and techniques to breach defenses while avoiding detection. Examples include exploiting vulnerabilities, privilege escalation, and lateral movement.Persistence and Exfiltration:
Test how long the attack can remain undetected and whether data exfiltration or operational disruption is possible.Reporting and Debriefing:
Document findings, including identified weaknesses and recommended mitigations. Share these insights with SOC teams to strengthen organizational defenses.
3. The SOC / SOC Engineering Process
SOC Engineering refers to the operational processes within a Security Operations Center (SOC) aimed at detecting, responding to, and mitigating cyber threats. Its workflow includes:
Detection:
Use tools like SIEM (Security Information and Event Management) systems to monitor for anomalous behavior, suspicious logs, or known indicators of compromise (IoCs).Triage and Analysis:
Investigate alerts to determine their validity and severity. This step involves correlating logs and events with CTI data to understand the context of a potential threat.Incident Response:
Contain, eradicate, and recover from identified incidents. For example, isolate infected devices, remediate vulnerabilities, and restore affected systems.Continuous Improvement:
Analyze incidents post-mortem to improve detection rules, response plans, and overall readiness.
4. Interconnections Between CTI, Red Teaming, and SOC Engineering
CTI and Red Teaming
CTI analysts provide Red Teams with actionable intelligence, including:
- Threat Actor Profiles: Detailed information on adversaries, their objectives, and their preferred TTPs.
- Targeted Asset Intelligence: Insights into the most critical organizational assets that attackers are likely to target.
- Emerging Threats: Early warning about new vulnerabilities or exploits that can be incorporated into Red Team exercises.
Red Teams, in turn, validate CTI by testing its relevance and identifying gaps in the organization’s understanding of potential threats.
CTI and SOC Engineering
CTI supports SOC Engineering by:
- Providing IoCs, TTPs, and threat context to enhance detection capabilities.
- Highlighting emerging threats that require updated detection rules or response playbooks.
- Offering feedback on how well SOC teams are detecting adversarial behaviors.
SOC engineers use this intelligence to develop detection logic, fine-tune SIEM alerts, and improve overall incident response effectiveness.
Red Teaming and SOC Engineering
Red Team exercises help SOC teams by simulating real-world attacks, generating logs that can be used to improve detection accuracy, and identifying gaps in response procedures. SOC teams can provide feedback to Red Teams, refining their simulations to better emulate real-world scenarios.
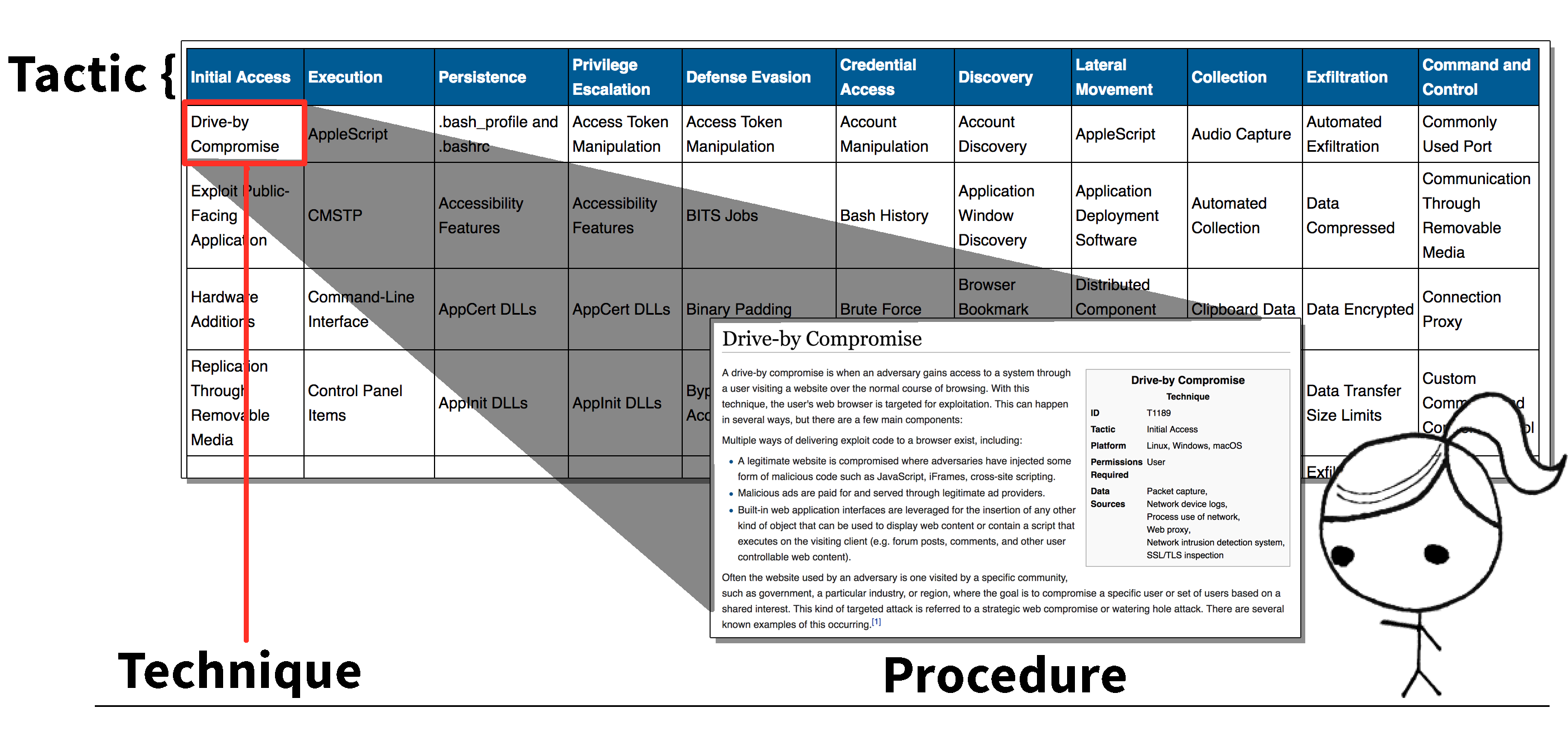
5. TTPs: The Backbone of Collaboration
Tactics, Techniques, and Procedures (TTPs) are a fundamental concept in cybersecurity. They describe how adversaries operate:
- Tactics: High-level goals or objectives (e.g., gaining initial access).
- Techniques: Specific methods used to achieve a tactic (e.g., phishing or exploiting vulnerabilities).
- Procedures: Detailed, step-by-step actions that describe how techniques are implemented.
TTPs are central to bridging the gap between CTI, Red Teaming, and SOC Engineering:
- CTI: Provides threat intelligence in the form of TTPs to describe adversary behaviors.
- Red Teaming: Uses TTPs to simulate attacks and test organizational defenses.
- SOC Engineering: Develops detection rules and response playbooks based on TTPs.
Challenges and Missing Links
Despite these frameworks, there are notable challenges:
For Red Teamers:
- Difficulty in translating TTPs from CTI into actionable simulations.
- Lack of centralized, practical resources for executing TTPs effectively.
For SOC Engineers:
- Challenges in interpreting attack logs and deriving meaningful detection insights.
- Limited collaboration with Red Teams to refine detection capabilities.
The Project TACTFlow: Bridging the Gaps
To address these issues, I’m creating this project called TACTFlow that will:
- Map MITRE ATT&CK TTPs to practical Red Team attack scenarios.
- Provide resources for simulating attacks based on CTI insights.
- Offer tools and techniques for SOC teams to improve their detection and response capabilities.
This initiative will be shared on my website (here ^^) and my GitHub too, covering TTPs in the context of CTI, Red Teaming, and SOC Engineering.
The goal is to create a comprehensive, practical resource for cybersecurity professionals to enhance their workflows and collaboration.
Resources
- https://attack.mitre.org/
- https://www.digifortex.com/Security-Services/Red-Team/
- https://redteam.guide/docs/Concepts/mitre_attack/
- https://www.trellix.com/security-awareness/operations/what-is-soc/
- https://www.memcyco.com/6-stages-of-the-threat-intelligence-lifecycle/
- https://www.optiv.com/explore-optiv-insights/blog/tactics-techniques-and-procedures-ttps-within-cyber-threat-intelligence